Continuing from our TLS enhancements introduced in Cerberus FTP Server 12.11, we are adding new key exchange and cipher options as shown in the screenshot below:
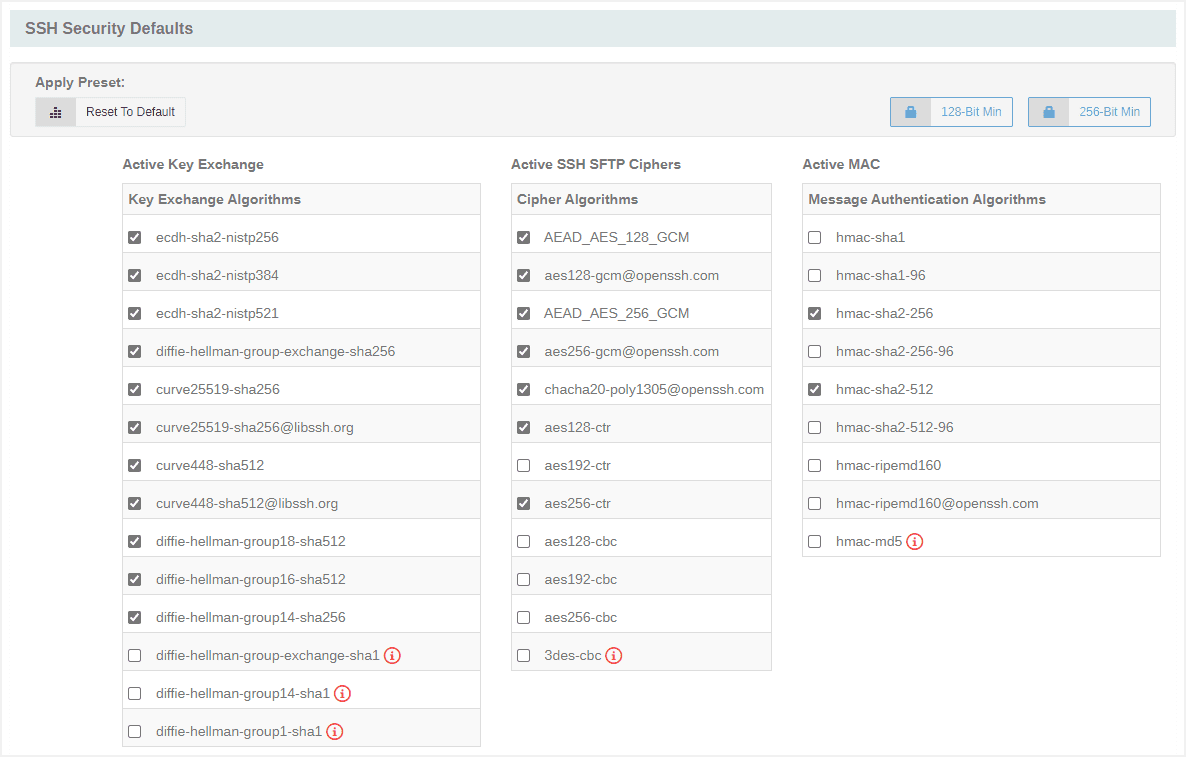
SSH Security Defaults
Key Exchange Algorithms
Version 13 adds Edwards Curves (x25519 and x448) to the supported list of KEXs. Cerberus supports both the final and the libssh versions:
- curve25519-sha256
- curve25519-sha256@libssh.org
- curve448-sha512
- curve448-sha512@libssh.org
Ciphers
Version 13 also adds additional Ciphers in both the final and openssh versions:
- AEAD_AES_128_GCM
- aes128-gcm@openssh.com
- AEAD_AES_256_GCM
- aes256-gcm@openssh.com
- chacha20-poly1305@openssh.com
ChaCha20 is not yet FIPS approved and so will not be available if FIPS Mode is enabled.
Certificates
In addition to the SSH options, Edwards certificates and keys (ed25519 and ed448) are now supported for both TLS & SSH.
Coming Soon
An upcoming release will provide additional support for CSR, self-signed certificate/key generation, and multiple SSH host keys.
These features are now available: Multiple Host Keys in SSH and Certificate Generation Enhancements.
Availability
These are just some of the new features that are now available in the Cerberus FTP Server 13.0 Professional and Enterprise editions. To learn more about all of the new features in Cerberus FTP Server 13.0, check out our release notes.
Need an MFT Solution for Your Scaling Business?
JSCAPE, also by Redwood Software, is the easy-to-use, secure MFT (managed file transfer) solution that redefines flexibility and security for modern digital landscapes. With support for any platform, protocol, and environment, JSCAPE simplifies file transfers, ensuring high availability and meeting stringent security and compliance requirements. It accommodates various deployment options, including MFTaaS, on-premises, and hybrid cloud environments. Visit the JSCAPE MFT Server product page to learn more.
As always, we would love to hear your feedback on how the upgrade to OpenSSL impacts your setup and users.