Note: Cerberus FTP Server 2024.2 includes an enhancement to these configuration settings, detailed in this post.
In Cerberus FTP Server 2024.1, we have added Two-Factor Authentication (2FA) support for SFTP and SCP. We support both time-based one-time password (TOTP) and Duo two-factor.
The small print. Since you cannot enroll in 2FA from an SFTP client, users have to either set up their TOTP/Duo through the Web Client (Enterprise Edition or above) or administrators can manually enroll users in Duo.
SFTP and SCP already support multi-factor authentication (MFA) using passwords and public keys, but this enhancement allows adding an additional factor to the password portion. We do not support 2FA with public keys alone.
Using 2FA with SSH SFTP/SCP
If a user has 2FA enabled as shown in the screenshot below, then they will be required to enter it for SFTP/SCP. Administrators can see 2FA status by selecting a user in User Manager : Authentication.
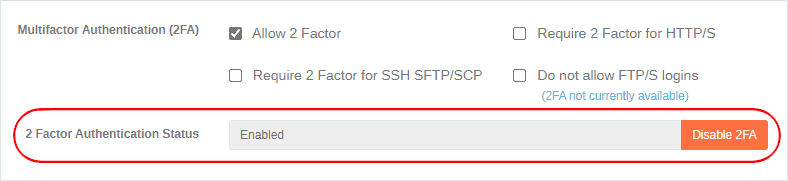
2FA Enabled for User
Administrators can also require 2FA by enabling the “Require 2 Factor for SSH SFTP/SCP” checkbox as shown in the screenshot below.
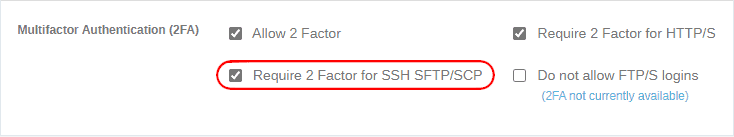
2FA Required
Duo Support
Cerberus can use any Duo supported interactive authentication method including push notifications, phone call, mobile and SMS OTP, hardware tokens and security keys with a display or in serial mode, and bypass codes.
Depending on the client, users will see a prompt where they can enter a passcode or select an external option. In the screenshot below, the user has requested SMS codes, and the system confirms they were sent and indicates which code is next.
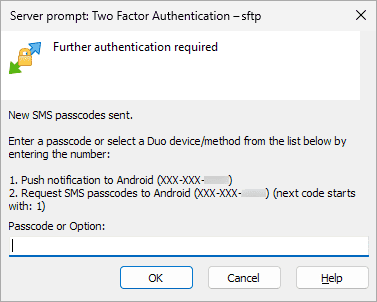
Duo Two Factor Prompt
TOTP Support
Cerberus supports many TOTP authenticators such as Google Authenticator and Microsoft Authenticator. TOTP authentication must be set up through the Web Client, so the user has to have logged in via HTTPS at least once. Depending on the client, users will see a prompt where they can enter their factor as shown in the screenshot below.
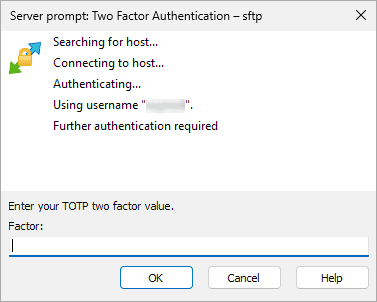
TOTP Two Factor Prompt
Client Support
In order to use 2FA, the SFTP client must support interactive login. Many of the most popular clients do such as OpenSSH, WinSCP, Filezilla, Cyberduck, and even the embedded Dropbear.
OpenSSH & Dropbear
The OpenSSH and Dropbear command line clients support interactive login smoothly and require no changes to have it dynamically enable 2FA as directed by the Cerberus Server.
WinSCP
The WinSCP GUI client does an excellent job with interactive login and is one of the best GUI clients for 2FA support. Like OpenSSH, no changes are required.
If you find that you activate push before having your device ready or a phone callback typically takes too long, you may find that WinSCP complains. This can be adjusted by editing the session and going to Advanced : Connection. The default 15 second “Server response timeout” can be adjusted as needed as shown in the screenshot below.
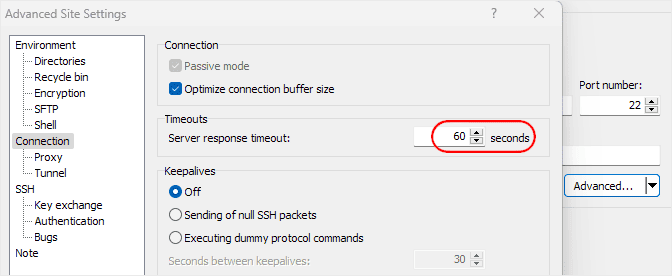
WinSCP Server response timeout
FileZilla
FileZilla requires a few adjustments for 2FA. First, to make interactive logins work, you first need to set the “Logon Type” to Interactive. You can find this setting in the Site Manager for a saved connection as shown in the screenshot below.
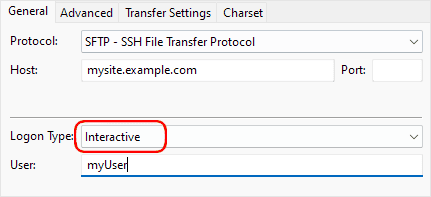
FileZilla Interactive Logon
FileZilla treats SFTP like a FTP and tries to open multiple connections rather than reusing the existing SSH channel. When using interactive mode, this means it prompts you to login on each file transfer. To make the client usable in this mode, enable “Limit number of simultaneous connections” and set “Maximum number of connections” to one (1) in the Transfer Settings tab as shown in the screenshot below.
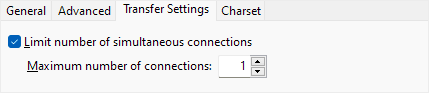
FileZilla Max Connections
Finally, FileZilla does not respect the newline characters provided in instructions and prompts as specified in RFC 4256. The information is all there, but it appears a bit more cluttered than in other clients. There is no known fix or setting for this issue.
Cyberduck
Cyberduck has a fixed authentication method loop which isn’t as flexible as RFC 4256 recommends. While full interactive login can be initiated first in Cyberduck, this has other side effects, and clients should follow the Server’s directions on when to activate interactive mode.
The first time through authentication, Cyberduck fails to prompt for 2FA; on the second try, it properly handles it. To eliminate this first failure, you can edit the .ssh/config file to add instructions for specific connections as shown in the excerpt below.
Host mysite.example.com PreferredAuthentications publickey,password
Like FileZilla, Cyberduck opens a new connection for each transfer. To make the client usable, open Edit : Preferences : Transfers : General and select “Use browser connection” in the Transfer Files dropdown as shown in the screenshot below.
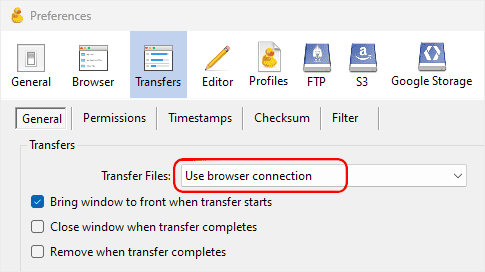
Cyberduck Use browser connection
Availability
SFTP and SCP are available in Cerberus FTP Server Professional Edition and above. Time-based One-time Password (TOTP) requires the Web Client for setup which is available in Enterprise Edition and above. Duo support is available in all editions, and the Duo Admin Panel offers additional methods for enrolling users that do not require the Web Client.
These are just some of the new features that are available in Cerberus FTP Server 2024.1 editions. To learn more about all the new features in Cerberus FTP Server 2024.1, check out our release notes here.
Looking for more? Dive deeper into the world of SFTP Two-Factor Authentication with our detailed guide on the JSCAPE blog. Like Cerberus, JSCAPE is part of the Redwood family and is dedicated to enhancing file transfer security through innovative solutions for growing enterprises. Learn more about the robust security measures in the blog titled: ‘What Is An SFTP?‘
As always, we look forward to hearing how our customers use integrations and how any improvements would help you set up and maintain Two-Factor authentication. We would love to hear your feedback.