In this post, we provide an overview of the CMMC requirements your organization will face from a data and file transfer perspective, along with how you can use tools like Cerberus FTP Server to help.
What is Cybersecurity Maturity Model Certification?
Cybersecurity Maturity Model Certification is a third-party validation of an organization’s efforts to conform to the data and information security standards documented in NIST SP 800-171 Rev 2 and NIST SP 800-172. These publications establish guidelines for an organization’s handling of data that falls under the category of Controlled Unclassified Information (CUI).
CUI is a special class of sensitive information that includes everything from witness protection program listings to NATO personnel to critical infrastructure plans. If your file transfer system processes or houses any of the data that appears on the complete list of Controlled Unclassified Information at this link, you will need to enact special data transfer compliance requirements to help protect the U.S. defense industrial base and sensitive critical infrastructure from cyber attacks.
What are the Cybersecurity Maturity Model Certification Levels?
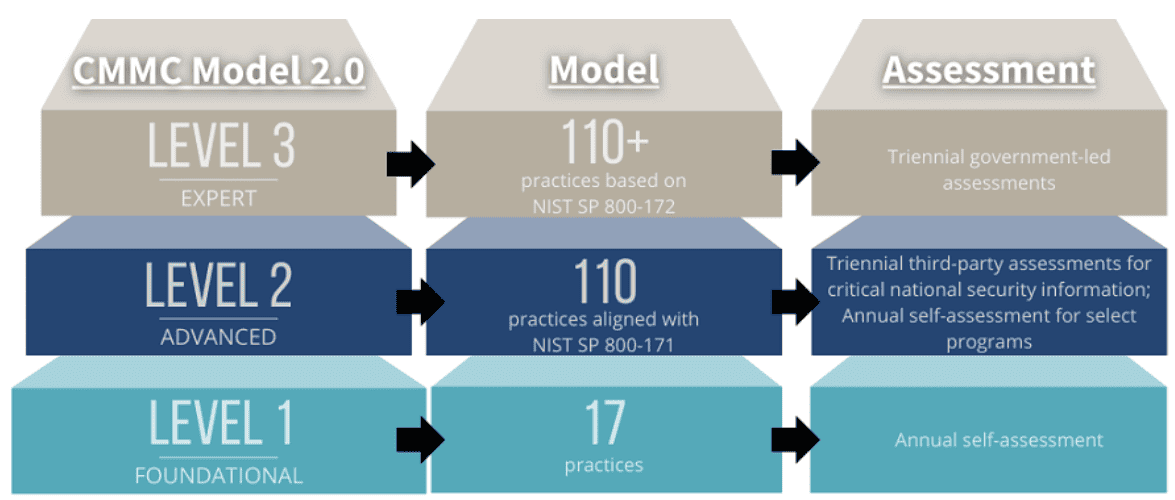
The current CMMC version 2.0 has three levels of certification:
Level 1 CMMC compliance most directly affects file transfer solutions, as these requirements include cybersecurity practices such as:
- Access controls
- Authentication requirements
- System and communications protection and integrity
- Periodic security scans
CMMC level 2 compliance extends to the complete list of NIST SP 800-171 requirements for the protection of CUI, which we’ve discussed in this companion blog post (link pending).
Level 3 compliance requires full implementation of the practices in NIST SP 800-172, which governs federal contact information.
What Companies Must Achieve CMMC?
Any organization operating as a prime- or sub-contractor for the DoD will be required to obtain a CMMC certification, regardless of the contractor’s size. This requirement also includes contractors who access, process or store contact information of any federal employee, such as payroll providers and benefit administrators. Collectively, these firms are referred to as the Defense Industrial Base (DIB).
How Can Companies Achieve CMMC?
The CMMC 2.0 rulemaking process has not yet concluded, but when it does, organizations will be required to attain either:
- A self-assessment (for Level 1 Certification)
- Certification from an accredited third party (for Level 2 Certification)
- Certification directly from the federal government (for Level 3 Certification)
How Does CMMC Apply to File Transfer?
To set up your file transfer system for CMMC, focus on the following areas:
1. Access Protection
Limit access to only authorized users and processes. Require every connection to authenticate and ensure that only authorized requests are approved. Ensure that you set up strict account access and password management policies to prevent phishing and brute force attacks.
Cerberus FTP Server’s access protection features are the ideal tool to help ensure compliance with this requirement, as they allow fine-grained security group and access permission trimming.
Our User Manager and managed password policy toolkit help ensure only the right people access your system
2. Data Encryption
FIPS 140-2 validated cryptography must be employed during all data access and transfer (Cerberus FTP Server is FIPS 140-2 validated).
3. Device Access
As an on-premise file-hosting solution, Cerberus FTP Server is an ideal choice to limit external data storage and processing (which can affect cloud providers). As well, Cerberus’s Server Manager allows administrators to restrict connections to only authenticated devices operating at the required level of encryption.