Welcome to another review of features in Cerberus FTP Server Version 12!
In this article, we explore Directory-Based Administration. This feature allows you to extend Cerberus Administration rights to Active Directory users and groups. This is a much-anticipated feature, available in Professional and Enterprise Edition, especially for those of you running Cerberus FTP Server in larger AD environments. When you use this feature:
- Administrators will no longer need a separate username/password for Cerberus FTP Server. The Web Admin Console will accept their standard Windows login and password.
- Provisioning new administrators is as easy as adding them to an AD group and giving them the Web Admin Console URL.
A Short Tour
Let’s take a look at some of the changes. It should feel very familiar if you’re already using AD for regular end-users. Note that these are pre-release screenshots; the user interface may change before release.
Create an Admin Directory Connection
Under AD Users, we’ve added a new type of AD Users configuration to support administrator accounts:
The Administrative Users settings are a slimmed-down version of the Standard Users configuration. Administrative Users do not receive automatic access to normal file services. As such, Virtual Directory, file-sharing permissions, and Directory Mapping options are omitted. The User MFA Settings still appears, as multi-factor authentication is a must-have for admin accounts:
Create Admin Users and Groups
Once an AD Admin Connection is created, admin rights can be extended to users and groups on that connection, all in one place. We’ve enhanced the Administrator Accounts area to support this. It is located, as before, under Server Manager, Remote, Remote Admin Settings:
The New button reveals an updated dialog for creating admin users. Choosing Administrator Type Native Admin creates an old-style admin account, whose details and credentials are managed entirely within Cerberus FTP Server:
The Administrator Type pull-down reveals a new item, Directory Admin:
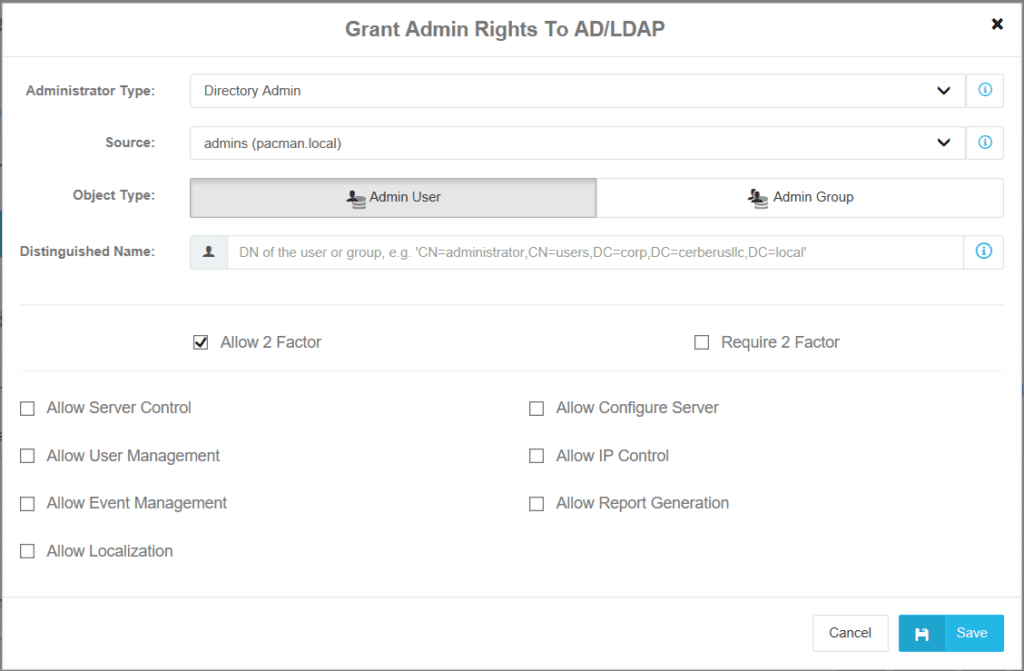
Directory Administrator Interface
This window for Directory Admin displays all the options you’ll need to grant Web Admin rights to directory-based users and groups:
- Source
The domain of the user/group to receive Admin access. The pull-down lists contains only AD Admin Connections. All Admin Connections appear in the pull-down, but most deployments will need only one.
- Object Type
Admin User grants access to a single domain user.
Admin Group grants access to all members of the group. Nested groups (and their members) also inherit the assigned permissions.
- Distinguished Name
The DN of the user or group, for example, “CN=DirAdmin,CN=Users,DC=mydomain,DC=com”
It is best to copy and paste from an AD administration tool like Active Directory Users and Groups or PowerShell cmdlets Get-ADUser and Get-ADGroup
The remaining options are common to Native Admins and control two-factor policy and fine-grained administrative rights:
- Allow 2 Factor, Require 2 Factor
Allow or Require users and groups to setup two-factor authentication.
- Permissions
Admin roles allowed to this user or group.
Edit Admin Users and Groups
We have enhanced the Administrator Accounts editor to support the new administrator types. Native Admins, Directory Users and Directory Groups appear together in the navigation table. The table icons and Source column help to distinguish between them. The selected row’s details are editable in the bottom panel.
Tie IT Together
With the right AD group organization, provisioning your IT professionals with admin access to Cerberus FTP Server admin is effortless. Let’s run through a simple use case to demonstrate.
Manage AD Groups
Our goal in this example is to grant full administrative access to the Cerberus FTP Server Web Admin Console across our entire IT organization. Assume that our IT professionals’ administrator accounts are members of the “All IT Administrators” group:
Following best practices, we create a Domain-local group “Cerberus Full Admin Access”…
…and we add “All IT Administrators” as a member:
Grant the AD Group Cerberus Admin Rights
Finally, we grant “Cerberus Full Admin Access” admin access, allowing all roles, within the Cerberus FTP Server Admin Console. We also enable Require 2 Factor for this Admin Group, as an added security measure:
Done
That’s really all there is to it! Now our whole IT organization can login to the Cerberus Web Admin Console with their normal Windows credentials:
Our example user successfully authenticates with their Windows credentials. Web Admin prompts the user to create a second factor for later authentication, per security requirements:
Once second-factor is accepted, Web Admin appears:
Provisioning and de-provisioning users is as simple as adding or removing from the “All IT Administrators” group.
Conclusion
Since adding support for AD and LDAP user accounts, many customers have requested the same functionality from the Web Admin Console. We are pleased to release this feature in Cerberus FTP Server Version 12, enabled in both Enterprise and Professional editions.
To learn more about all of the new features in Cerberus FTP Server 12.0, check out our release notes here
Have comments or questions? Please leave them below!