What are FTPS and SFTP?
File transfer protocol secure (FTPS) and secure shell file transfer protocol (SFTP) both support secure file transfer, but they rely on entirely different protocols and operate in fundamentally different ways. FTPS is an extension of the traditional FTP protocol that adds encryption through secure sockets layer (SSL) or transport layer security (TLS) and secures the data connection and authentication process while still using the same basic architecture. SFTP, by contrast, is built on the secure shell (SSH) protocol and uses a single port for all communication to offer a more streamlined and firewall-friendly approach to secure file transfer protocol operations.
Because both include encryption and sound similar by name, it’s easy to confuse FTPS and SFTP. However, they differ in port usage, authentication methods and overall compatibility with various operating systems and network protocols. It’s crucial that you understand their differences when deciding whether to use FTP with SSL/TLS enhancements or adopt a fully integrated SFTP server that runs over SSH. This distinction becomes even more important in environments focused on cybersecurity, firewall configuration and efficient managed file transfer (MFT) workflows. Explore what makes them different, when and how to properly use FTPS and SFTP and how to implement them in your organization’s secure file transfer processes.
Key differences between FTPS and SFTP
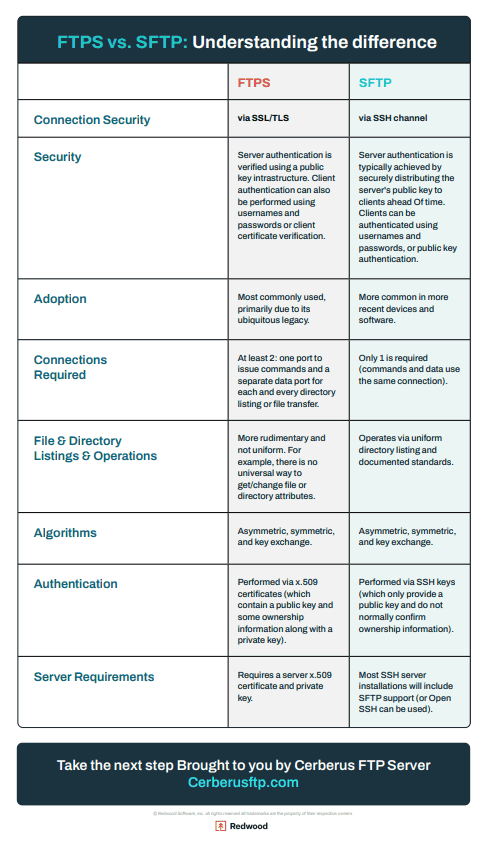
The table below breaks down the key differences between FTPS and SFTP across key areas like connection security, authentication methods, port usage and overall compatibility. These differences influence everything from firewall configuration to platform support and data transfer performance.
| FTPS | SFTP | |
|---|---|---|
| Connection Security | via SSL/TLS | via SSH channel |
| Security | Server authentication is verified using a public key infrastructure. Client authentication can also be performed using usernames and passwords or client certificate verification. | Server authentication is typically achieved by securely distributing the server’s public key to clients beforehand. Clients can be authenticated using usernames and passwords or public key authentication. |
| Adoption | Remains in use within legacy systems and industries with entrenched infrastructure, but adoption is steadily declining due to firewall complexity and reliance on SSL/TLS certificates | Continues to gain widespread adoption across cloud platforms, DevOps pipelines and modern applications thanks to its simplicity, firewall-friendliness and built-in support across operating systems and development tools |
| Port Connections Required | At least two: one port to issue commands and a separate data port for each directory listing or file transfer | Only one is required (commands and data use the same connection) |
| File and Directory Listings and Operations | More rudimentary and not uniform. For example, there is no universal way to get/change file or directory attributes. | Operates via uniform directory listing and documented standards |
| Algorithms | Asymmetric, symmetric, and key exchange. | Asymmetric, symmetric, and key exchange. |
| Authentication | Performed via x.509 certificates (which contains a public key and some ownership information along with a private key) |
Performed via SSH keys (which only provide a public key and do not typically confirm ownership information) |
| Server Requirements | Requires a server X.509 certificate and private key. | Most SSH server installations will include SFTP support (or Open SSH can be used) |
Overall, FTPS is better suited if your organization needs strong certificate-based authentication, works in Windows-based environments or must maintain compatibility with older systems that still use FTP. SFTP, on the other hand, is ideal for modern networks which often prioritize single-port connections and simplified firewall traversal (with the advantage of native support across Linux, Unix and cloud platforms).
FTPS vs. SFTP: Use Case Comparison
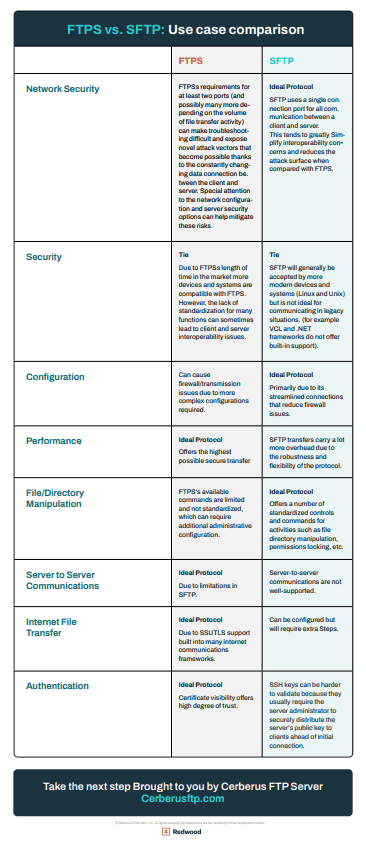
The table below can help you choose between FTPS and SFTP based on your use case.
| FTPS | SFTP | |
|---|---|---|
| Network Security | FTPS’s requirements for at least two ports (and possibly many more depending on the volume of file transfer activity) can make troubleshooting difficult and expose novel attack vectors that become possible thanks to the constantly changing data connection between the client and server. Special attention to the network configuration and server security options can help mitigate these risks. | Ideal Protocol SFTP uses a single connection port for all client and server communication. This tends to greatly simplify interoperability concerns and reduces the attack surface compared to FTPS. |
| Compatibility | Tie Due to FTPS’s length of time in the market, more devices and systems are compatible with FTPS. However, the lack of standardization for many functions can sometimes lead to client and server interoperability issues. |
Tie SFTP will generally be accepted by more modern devices and systems (Linux and Unix) but is not ideal for communicating in legacy situations. (for example, VCL and .NET frameworks do not offer built-in support) |
| Configuration | FTPS can cause firewall/transmission issues due to more complex configurations required. | Ideal Protocol Primarily due to its streamlined connections that reduce firewall issues. |
| Performance | Ideal Protocol Offers the highest possible secure transfer speeds. |
SFTP transfers carry a lot more overhead due to the robustness and flexibility of the protocol. |
| File/Directory Manipulation | FTPS’s available commands are limited and not standardized, which can require additional administrative configuration. | Ideal Protocol Offers several standardized controls and commands for activities such as file directory manipulation, permissions locking, etc. |
| Server to Server Communications | Ideal Protocol Due to limitations in SFTP |
Server-to-server communications are not well-supported |
| Internet File Transfer | Ideal Protocol Due to SSL/TLS support built into many internet communications frameworks |
Can be configured but will require extra steps. |
| Authentication | Ideal Protocol Certificate visibility offers a high degree of trust |
SSH keys can be harder to validate because they usually require the server administrator to securely distribute the server’s public key to clients ahead of initial connection |
When to use FTPS vs. SFTP: Real-world use case comparisons
While the technical differences between FTPS and SFTP are important, the real decision often comes down to the environment you’re working in and the requirements of your organization’s file transfer workflows. Your choice of protocol will impact firewall configuration, authentication methods, compatibility and long-term supportability. Below are common use cases where one secure file transfer protocol tends to be a better fit than the other, based on how your organization prefers to handle data connections, security and network protocol behavior.
Use case 1: Minimize firewall configuration and port usage
Choose SFTP
- SFTP: This protocol uses a single port (typically TCP port 22), which makes it easier to deploy behind strict firewalls or within NAT environments. All communication, including commands, authentication and data transfer, flows through this single connection, which reduces the need for complex firewall
- FTPS: In contrast, this protocol requires at least two open ports: one for the control connection and one (or more) for each data channel, depending on whether it uses active or passive mode. This setup can create challenges for firewall traversal and increase your organization’s cybersecurity exposure due to the data channel often being opened on a dynamic port number in passive mode.
Use case 2: Require certificate-based authentication
Choose FTPS
- FTPS: This protocol supports x.509 certificates, which allow both server and FTP client authentication using verifiable certificate chains. Organizations that require clients to validate their identity or link with enterprise authentication methods will find FTPS’s client-side SSL certificates to be the ideal choice.
- SFTP: This protocol supports SSH keys and public key authentication, but it does not use SSL, TLS or certificate-based validation. If your environment requires detailed certificate management, FTPS is the more appropriate choice.
Use case 3: Regulated environments (e.g., HIPAA, PCI-DSS)
Both SFTP and FTPS can work
- Both FTPS and SFTP can meet data encryption and access standards specified in regulations such as HIPAA or SOX and guidelines like PCI-DSS, but full regulatory compliance requires correct configuration outside of just your file transfer server.
- SFTP is often favored for its simplicity, especially in automation and cloud-based environments where single-port connections reduce the risk surface.
- However, FTPS may be a better fit when regulations require certificate chains or detailed control over SSL/TLS
- In either case, secure authentication, strong ciphers and well-maintained FTP server infrastructure are key to compliance.
Use case 4: Legacy system compatibility
Choose FTPS
- FTPS: If you’re supporting older systems or integrating with legacy software, FTPS is probably the better option. It’s built on the traditional FTP protocol, which makes it compatible with older middleware, Windows-based tools and systems that still use FTP as a foundation.
- SFTP: This protocol may not work in environments that lack SSH support or where FTP support is hardcoded into existing solutions.
Use case 5: Cloud/modern IT environments
Choose SFTP
- SFTP: This protocol aligns better with modern IT ecosystems, including Linux and Unix-based systems, secure APIs and DevOps workflows. It integrates easily into cloud-native platforms, CI/CD pipelines and containerized deployments. Because it’s built on the SSH protocol, SFTP offers built-in support in most operating systems and removes the need for external SSL certificate management.
- FTPS: This protocol requires more involved firewall configuration, multiple TCP ports and external SSL/TLS certificate handling, which can complicate deployment in dynamic or cloud-hosted environments. Many organizations are also moving away from FTPS support as SFTP becomes a modern standard.
Use case 6: Business user simplicity
Choose SFTP
- SFTP: If your teams don’t have deep technical knowledge, SFTP offers a cleaner setup and fewer connection issues. Its use of a single port means fewer network problems, while SSH file transfer protocol tools are widely available and easy to configure.
- FTPS: Although this protocol is powerful, it may require more ongoing support, especially in environments with strict firewall rules or complex network configurations.
Use case quick reference table:
| Use case | FTPS | SFTP | Best choice |
|---|---|---|---|
| Strict firewalls | ❌ | ✅ | SFTP |
| Certificate auth | ✅ | ❌ | FTPS |
| HIPAA/PCI | ✅ | ✅ | Both |
| Legacy systems | ✅ | ❌ | FTPS |
| Cloud workloads | ❌ | ✅ | SFTP |
| Ease of use | ❌ | ✅ | SFTP |
Whether your organization prefers the certificate-driven model of FTPS or the firewall-friendly simplicity of SFTP, Cerberus FTP Server by Redwood supports both protocols and gives you the flexibility to meet your organization’s security, compliance and performance needs with confidence.
FTPS vs. SFTP: Pros and cons
Choosing between FTPS and SFTP comes down to your organization’s specific environment, security requirements and compatibility needs. Both options support secure file transfer using different network protocols. FTPS uses SSL/TLS, and SFTP uses SSH. Use this breakdown to help you decide which protocol better aligns with your organization’s use case, infrastructure and long-term file transfer strategy.
When to choose FTPS
FTPS is the better choice if your organization:
- Adheres to regulatory standards or internal policies that require the use of SSL/TLS
- Needs certificate-based authentication using x.509 certificates
- Operates in a Windows-heavy environment with existing FTP server support
- Uses infrastructure that includes legacy systems or older FTP-ran applications
- Wants clearer visibility into certificate ownership through public key infrastructure
FTPS works well in environments where backward compatibility, detailed authentication methods or direct integration with older file sharing workflows is a priority.
When to choose SFTP
SFTP is the better option if your organization:
- Is implementing secure automation or integrating MFT into DevOps pipelines
- Needs a single-port, firewall-friendly solution that simplifies data transfer
- Prioritizes firewall configuration, especially in environments using NAT
- Wants flexible support for SSH keys, scripting via command-line or API-based workflows
- Works with Linux, Unix or cloud-native platforms
SFTP excels in modern IT ecosystems and offers native secure file transfer protocol capabilities and easier deployment in dynamic or distributed networks.
Which is more secure: FTPS or SFTP?
Both protocols offer strong encryption and can support enterprise-grade cybersecurity, but they do so through different encryption schemes. FTPS uses TLS or SSL to encrypt both the control and data channels; this makes it secure as long as it’s properly configured. However, misconfigurations or skipped TLS handshakes can expose plain-text data or weaken authentication.
SFTP provides secure data transfer by default through a single connection. It avoids common vulnerabilities related to separate data channels, port negotiation or complex firewall traversal. If your organization values simplicity, tight port control and modern authentication methods using SSH keys or private keys, SFTP can deliver a more secure and maintainable option over time.
Visual comparison: FTPS vs. SFTP
Need to understand the differences in these file transfer protocols at a glance? The graphics below may help.
How FTPS and SFTP evolved: A brief history
To fully understand the key differences between FTPS and SFTP, it helps to look at how each protocol emerged. While both enable secure file transfers, they came from different origins: FTPS evolved as an encrypted extension of the traditional FTP protocol, while SFTP was built from the ground up as part of the SSH framework with security by design.
Origins of FTPS (extension of FTP)
As the first networking protocol that allowed file transfer from one machine to another, FTP predates the internet and was developed before security concerns about unauthorized users eavesdropping on data traffic needed to be considered.
As more and more people began using the web in the 1990s, the security and privacy of data transmission became legitimate concerns. This situation led to the development of the early SSL cryptographic protocol, which encrypts commands and data exchanged between a client and a server. When FTP transfers began using this layer in 1996, “FTPS” was born.
Origins of SFTP (as part of SSH-2)
SFTP evolved from a separate open-source file transfer protocol developed to transfer data within an encrypted format by default. Known as the SSH cryptographic network protocol, it was originally released in 1995 as freeware by a Swedish researcher attempting to secure his school’s network. After seeing SSH’s popularity and potential, the Internet Engineering Task Force soon began working to standardize the SSH protocol. These efforts extended into secure file transfer, and the first non-proprietary release of the SSH file transfer protocol came in 2001.
Various iterations and improvements led to SSH version two’s release in 2006, and SFTP has since become a widespread data transfer standard.
Deprecation of older FTP/SFTP versions
As security standards have advanced, older versions of FTP, FTPS and SFTP have gradually fallen out of favor due to known vulnerabilities and a lack of modern encryption support. Unencrypted FTP connections are now widely considered insecure because they transmit data in plain text. Similarly, outdated SSL protocols and early versions of TLS used in legacy FTPS setups have been deprecated in many environments to comply with modern cybersecurity requirements.
For SFTP, the shift toward SSH-2 marked a major improvement in both security and functionality. Early proprietary or first-generation implementations lacked standardized algorithms, limited authentication methods and offered poor compatibility across operating systems. Today, best practices recommend using only SSH version two and disabling legacy protocols to ensure secure, compliant and future-proof file transfer protocol deployments.
FTPS vs. SFTP for compliance
For IT leaders and security teams operating in regulated industries, the choice between FTPS and SFTP often comes down to which protocol aligns best with frameworks and regulations like PCI-DSS, HIPAA, GDPR and NIST’s FIPS 140-3. Both protocols can support compliant secure file transfer when properly implemented, but their differences in architecture, authentication methods and encryption protocols may affect how easily they integrate with existing compliance workflows. When you know these nuances, you can avoid audit failures and ensure long-term compliance with data protection standards.
PCI-DSS, HIPAA, GDPR and NIST considerations
Each of these frameworks mandates strong encryption, secure authentication and protection against unauthorized access during data transfer:
- PCI-DSS requires secure transmission of cardholder data, which both FTPS and SFTP can support. However, organizations must disable insecure protocols (like plain FTP or SSL v2/v3), enforce strong TLS or SSH encryption and maintain strict firewall configuration.
- HIPAA emphasizes the confidentiality and integrity of electronic protected health information (ePHI). Both protocols meet this need when configured with strong ciphers and access controls.
- GDPR requires data security “by design and by default.” Either protocol may comply if it protects personal data in transit and includes adequate user ID management and access control.
- NIST guidelines require certain cipher strengths implemented by validated cryptographic modules when protecting sensitive information on federal systems or defense networks.
The key to compliance lies not in choosing one protocol over the other, but in implementing secure configurations, disabling outdated cryptographic standards and documenting authentication, permissions and audit trails.
Which protocol is more commonly used in regulated industries?
SFTP tends to be more common in highly regulated environments due to its simplicity, modern design and use of a single port, which makes it easier to control and audit. Its reliance on SSH instead of SSL/TLS eliminates the need to manage certificate chains, and this can reduce your organization’s administrative overhead in secure file transfer protocol environments.
That said, FTPS remains widely used in industries with long-standing infrastructure, especially where x.509 certificate-based authentication is a requirement or where FTP support is already embedded in legacy systems. Industries like finance, healthcare and government may support both protocols but often favor SFTP when setting up new systems for MFT, auditability and streamlined cybersecurity policy enforcement.
FAQs: FTPS vs. SFTP
Is FTPS more secure than SFTP?
FTPS and SFTP both offer strong encryption and secure authentication methods, but neither is universally more secure than the other. Their level of security depends on how you configure them. FTPS relies on SSL or TLS to encrypt its control and data channels, while SFTP uses a single encrypted channel based on the SSH protocol. If you misconfigure FTPS, it transmits credentials before establishing a TLS handshake and may expose sensitive data. SFTP encrypts everything by default from the moment the connection begins, which minimizes the chance of plaintext exposure.
SFTP usually has fewer misconfiguration risks due to its single connection model and simplified firewall setup. FTPS, with its multiple TCP port requirements and separate data channels, requires more attention to firewall configuration and secure certificate management. When you deploy them correctly, both protocols can meet enterprise-grade cybersecurity and compliance standards like HIPAA, PCI-DSS or GDPR, but SFTP’s design tends to make it easier to deploy securely.
Why would someone still use FTPS instead of SFTP?
Many organizations continue to use FTPS because of its longstanding presence in enterprise environments and its compatibility with legacy systems and applications. FTPS builds on the traditional FTP protocol, which makes it easier to integrate with older software that already supports FTP connections. It’s also widely supported in Windows-based environments and is embedded into existing middleware or vendor tools that don’t offer native SFTP server functionality.
FTPS is also preferred in situations where certificate-based authentication is required. Its use of x.509 certificates provides a formal public key infrastructure that enables higher trust visibility between clients and servers, which is something SSH keys in SFTP do not provide out of the box. In regulated industries where private key ownership needs to be verifiable through certificate chains, FTPS may be the required protocol.
Which is faster: FTPS or SFTP?
In terms of raw transfer speeds, FTPS can be faster than SFTP under certain conditions because it allows for parallel data connections and has less encryption and packet validation overhead in protocol design. FTPS supports streamed transfers with optimized TCP behavior, and it doesn’t include some of the robust features that add processing overhead in SFTP, such as granular file attribute handling or permissions management. This can lead to better throughput in high-volume environments, especially when optimized on both ends.
However, SFTP often performs better in real-world scenarios where firewalls, NAT or security policies restrict open port ranges. Because SFTP uses a single port for all communication, it avoids the latency and connection negotiation overhead that can occur with FTPS in passive mode. So while FTPS might have the edge in ideal lab conditions, SFTP is often more reliable and consistent in complex or cloud-based environments.
Does FTPS use SSL or TLS?
FTPS was originally designed to use SSL for encryption, but SSL is now deprecated due to known vulnerabilities and cryptographic weaknesses. Modern FTPS implementations use TLS, which is the secure and recommended successor to SSL. TLS 1.2 and TLS 1.3 are the current standards in most environments and are required to meet compliance regulations, such as PCI-DSS.
When someone refers to FTP over SSL, they are typically referencing FTPS, but in secure environments, administrators should ensure their FTP server only permits TLS, not legacy SSL versions. Disabling outdated algorithms, enforcing strong ciphers and requiring encrypted sessions on both the control channel and data channel are all essential FTPS configuration best practices for maintaining a secure posture. Ready to see which protocol works best in your environment? Get a free demo of Cerberus FTP Server and explore secure, flexible file transfer built for modern IT and compliance.