Starting in version 12.11, Cerberus FTP Server will use OpenSSL 3 which provides the following benefits:
- Extends FIPS 140-2 validation until September 2026
- Adds TLS 1.3 protocol support
- Adds additional key exchange, cipher, and mac algorithms
Breaking Changes
If you are in FIPS mode, please read the FIPS section below as some older encryption elements have been disallowed that may prevent users with older client applications from connecting. In particular, TLS 1.0, TLS 1.1, and SSH ssh-rsa and ssh-dsa host keys and diffie-hellman-group1-sha1 are no longer allowed. We encourage customers who have FIPS enabled to upgrade their SSH SFTP clients to the latest versions prior to upgrading to Cerberus 12.11. For more information, please refer to our support page discussing the ssh-rsa and ssh-dsa host key issue.
In addition, the PFX format allows RC2-CBC encryption, which is not compliant with FIPS, HITECH-HIPAA or PCI DSS. This affects both FIPS and non-FIPS configurations. Most operating systems removed the RC2 algorithm from their systems years ago (Microsoft Windows in 2017) and only offer the TripleDES and AES256 algorithms, but the DigiCert tool only uses RC2. We encourage customers who are using the PFX format for their certificate to reference our support page discussing this issue and solutions prior to upgrading to Cerberus 12.11.
FIPS
Previous versions of Cerberus used OpenSSL 1.0.2 as it was the only version with an OpenSSL vendor requested FIPS 140-2 validation certificate. However, since version 1.0.2 is no longer in development and extended support will end at some point, we began working on integrating OpenSSL 3 into Cerberus when validation was submitted in September 2021. In August 2022, OpenSSL 3 was issued FIPS 140-2 validation certificate #4282 by NIST & CSE. This certificate has a sunset date of September 21, 2026, which means clients using FIPS in Cerberus version 12 won’t have to upgrade to version 13 when the current certificate sunsets on December 2, 2023.
There are a few changes that come with the updated FIPS provider in OpenSSL 3.
- TLS 1.0 and TLS 1.1 require SHA-1 for signature generation which is no longer allowed due to collision weaknesses in SHA-1. Cerberus does not support any FIPS approved cipher suites for these protocols and they will be disabled in FIPS mode. (See Table 8 in NIST 800-131A Revision 2 and Table 3 in NIST 800-57 Part 1 Revision 5)
- For SSH, a major change is that ssh-rsa and ssh-dsa host keys are no longer allowed as they also require SHA-1. (See Table 8 in NIST 800-131A Revision 2; for technical discussion see RFC 8332)
- For SSH, diffie-hellman-group1-sha1 is no longer allowed as it uses an RSA key with only 1024 bits (a minimum of 2048 bits is now required). (See Table 4 in NIST 800-131A Revision 2)
In addition, we have added warnings for:
- The Key Exchange diffie-hellman-group-exchange-sha1 is considered weak. (See RFC 9142)
- The Key Exchange diffie-hellman-group14-sha1 is considered weak, but allowed for Legacy use. (See RFC 9142)
- Triple DES will be deprecated soon due to the SWEET32 birthday attack. (See Update to Current Use and Deprecation of TDEA)
If a legacy connection is required, RFC 9142 recommends using diffie-hellman-group14-sha1 as the strongest of the SHA-1 based options.
For more information on FIPS 140-2, see our “What is Fips 140-2” page.
What’s New
The biggest immediate impact for clients is that TLS 1.3 is now a protocol option for TLS based transfers, including FTP/S, HTTPS, and SOAP. TLS 1.3 will be automatically enabled for transfers and SOAP.
At this time, TLS 1.3 supports five cipher suites:
- AES128 GCM SHA256
- AES256 GCM SHA256
- CHACHA20 POLY1305 SHA256
- AES128 CCM SHA256
- AES128 CCM8 SHA256
The last two require an ECDSA certificate and are not widely supported and therefore are not enabled by default.
Other notable new capabilities for TLS 1.2 include ARIA and ChaCha20-Poly1305 cipher suites.
Although each configuration will be unique, in our testing, we have found OpenSSL 3.0 has a faster connection setup time resulting in lots of smaller transfers being faster overall than with 1.0.2. We’d love to hear about your setup, usage cases, and results, so send us some feedback.
Configuring features
We’ve updated the main and SOAP TLS settings pages; these can be accessed from Server Manager / Security / Advanced TLS and Server Manager / Remote / SOAP TLS Settings respectively.
The TLS 1.2 and below and TLS 1.3 sections now have information dropdowns when you click on the blue icon to the right of Cipher Strings and Cipher Suites that describe the format, defaults, and some options for each string.
The Testing section now has a Refresh Cipher List that updates the list of cipher suites that will be activated by the enabled protocols and requested cipher strings. As you make changes to the various selections, just click refresh to see what the cipher list will contain.
The ‘Advanced TLS Security Settings’ screenshot shows the updated page layout.
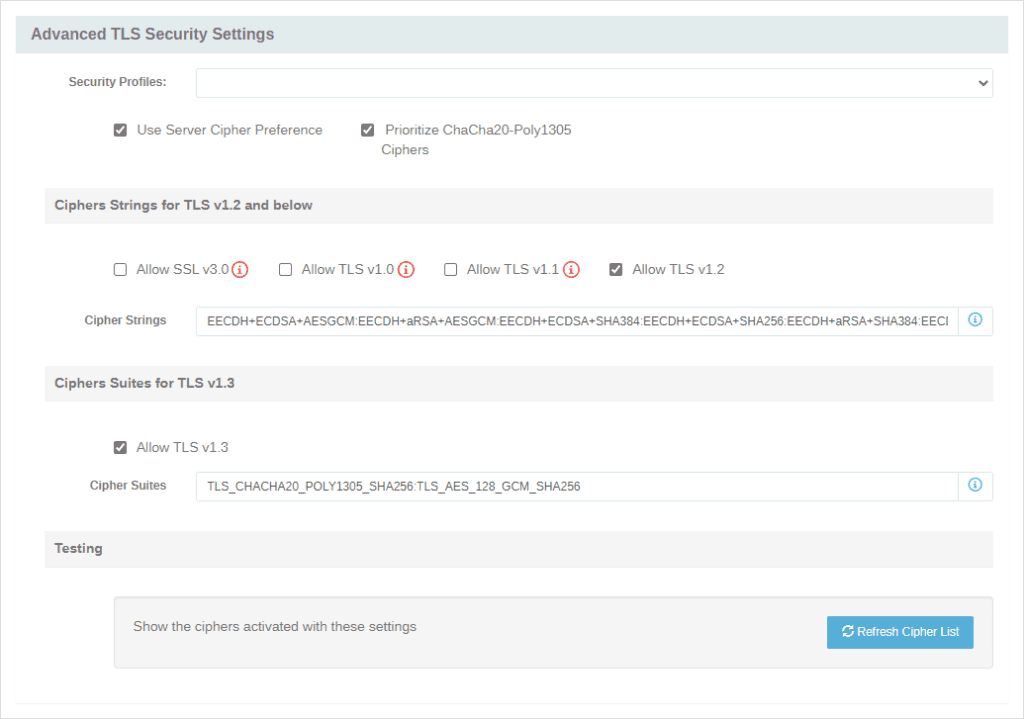
One last perk for administrators with users transferring files from older mobile phones without built-in AES support; the new checkbox “Prioritize ChaCha20-Poly1305 Ciphers” will allow configurations with “Use Server Cipher Preference” enabled to use ChaCha20-Poly1305 when a device offers it at a higher client preference due to power and speed concerns. NOTE: ChaCha20-Poly1305 is not available in FIPS mode.
Upgrade Notes
Some security changes were made in OpenSSL 3 which will impact clients still enabling TLS 1.0 and TLS 1.1; these now only work at security level 0 except when RSA key exchange without SHA1 is used which Cerberus does not support. In addition, X509 certificates signed using SHA1 will no longer be trusted without setting the security level to 0.
Cerberus currently achieves similar goals as the security level using the Security Profiles dropdown. To maintain compatibility with previous versions of Cerberus, we automatically set the security level to zero. Administrators can override this by adding @SECLEVEL=x to the Cipher Strings; x can be 0 to 5. Level 1 is OpenSSL’s default requiring at least 80 bits of security; Level 2 requires 112 bits; Level 3 requires 128 bits, Level 4 requires 192 bits; and Level 5 requires 256 bits of security.
For new installs, TLS 1.0 and 1.1 will be disabled by default.
Coming Soon
Upgrading to OpenSSL 3 also allows us to add some additional features which will arrive in the coming months. Such as:
- SSH will support x25519 and x448 key exchange, AES GCM encryption and digest, and ChaCha20 Poly1305 encryption and digest.
- Edwards certificates and keys (ed25519 and ed448) will be supported for TLS & SSH.
These features are now available: Cerberus FTP Server 13.0 Introduces Enhanced SSH Options.
Availability
These are just some of the new features that are now available in Cerberus FTP Server 12.11 editions. To learn more about all of the new features in Cerberus FTP Server 12.11, check out our release notes.
As always, we would love to hear your feedback on how the upgrade to OpenSSL impacts your setup and users.