Introduction
Cerberus is receiving a security update with version 11.2 that administrators should review before upgrading. There is a small chance that the changes made may impact services, but we have provided an override setting to workaround any impact. Administrators using Event Manager should make configuration changes to keep their event settings as secure as possible.
Summary
Prior to this release, some outgoing SSL/TLS connections did not perform certificate or host name verification. While these connections did use SSL/TLS to prevent passive eavesdropping, the remote host’s identity was not verified through PKI.
After upgrading to 11.2, all outgoing connections will be verified using the operating system’s list of trusted certificates. As such, remote servers must present a valid certificate signed by a trusted authority. Also, the host name used to connect to the server must pass verification against the names in the certificate.
It is important to note that this impacts only a subset of outgoing connections initiated by Cerberus FTP Server. These features may be affected:
-
- Check for Updates
Cerberus opens a connection to our company servers to see if an upgrade to the software is available.
Cerberus company servers are signed by well-known and trusted certificate authorities, so we do not anticipate any issues. - reCAPTCHA
Cerberus FTP Server connects to Google for reCAPTCHA set up.
Google servers are generally trusted by the OS, so we do not anticipate any issues. - HTTP and SMTP Targets
Through Event Manager, Cerberus FTP Server can be configured to automatically send emails or post data to remote servers.
Administrators will need to enable certificate verification on their pre-existing HTTP and SMTP targets to improve security.
- Check for Updates
Configuration Changes
We have added options to Server Manager / Security / Server Verification and to Event Manager / Event Targets to help Cerberus administrators manage these settings.
Server Manager
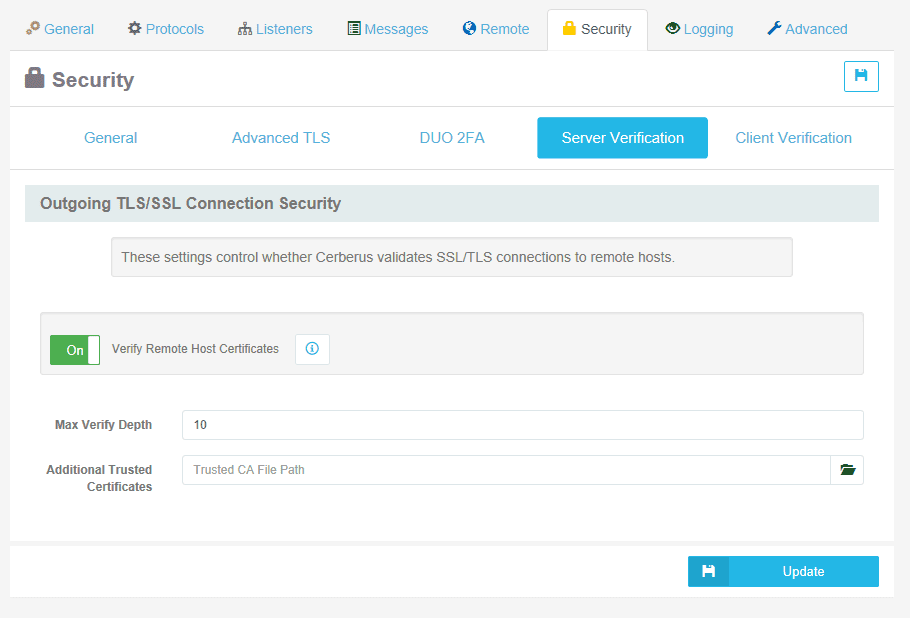
Server Manager / Security / Server Verification contains three new configuration options:
- Verify Remote Host Certificates
Turning Server Verification off is global, overriding all other settings throughout Cerberus.
Turning verification off is the less secure option and is only provided as a temporary fail-safe, such as a certificate issue causing a critical service outage. - Max Verify Depth
This determines how many issuer certificates Cerberus will follow when verifying.
Administrators may increase this value if remote hosts have long certificate chains. - Additional Trusted Certificates
Administrators may provide a path to a PEM file containing additional certificates that Cerberus should trust when verifying remote servers.
Use this option when Cerberus should trust certificates that cannot or should not be imported to the operating system certificate store.
Event Manager
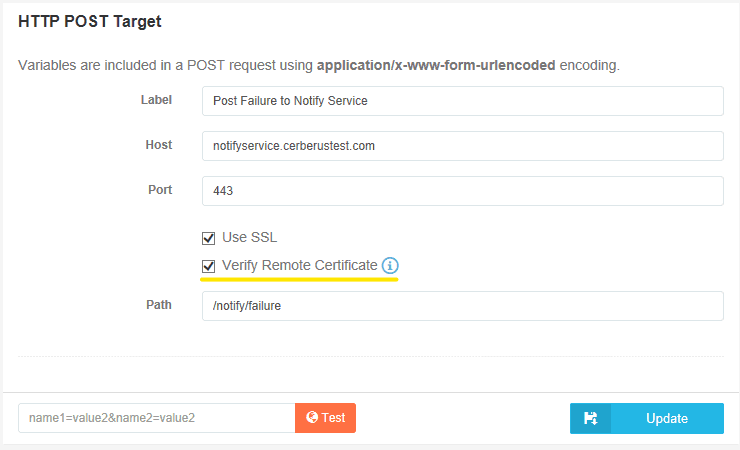
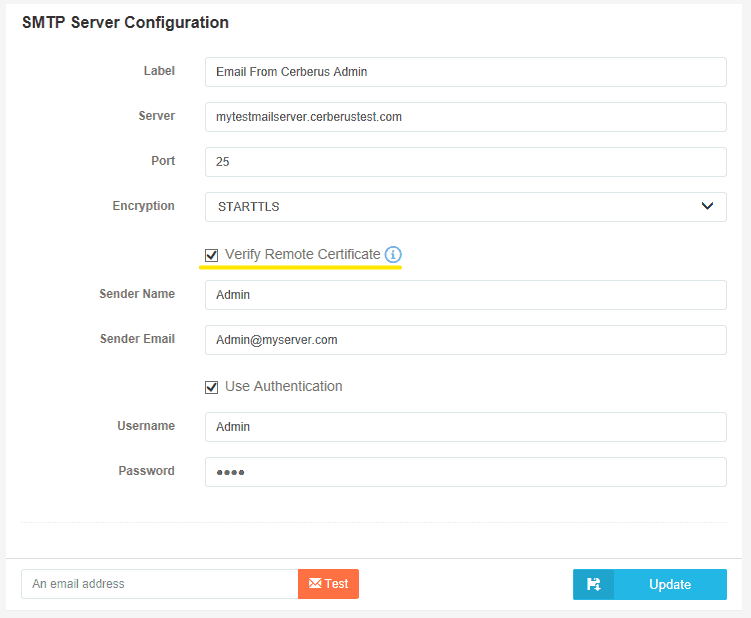
HTTP Post Target and SMTP Server Target actions contain one new configuration option:
- Verify Remote Certificate
Use this to enable or disable Server Verification for this Action Target. This defaults to ‘enabled’ for new actions, and is set to ‘disabled’ for action targets that exist prior to upgrading to 11.2.
Cerberus Administrators using Event Manager are urged to examine their HTTP and SMTP targets and enable certificate verification wherever possible.
Conclusion
We hope you share our excitement about the new features we are adding to Cerberus. It’s always challenging to improve a product’s security without impacting existing deployments, but we believe that giving Cerberus administrators the power and flexibility to make sensible security decisions is the right choice.